Prevent intrusion with Fail2ban
Some people are using Fail2ban, and some are using DenyHosts - i like Fail2ban because the configuration is simpler, and it can be used for more than SSH. DenyHosts is only for SSH.
Fail2ban is a program/framework to prevent intrusion. It is blocking ip-addresses by adding records in your iptables with a DROP action based on log-file reading.
Installation and setup
Start with installing Fail2ban from the Debian repositories:
$ sudo apt-get install fail2ban
When installed, you can find it's configuration files in diretory /etc/fail2ban, so cd into this directory:
$ cd /etc/fail2ban/
What you need to edit here is the jail.conf-file, which holds the essential configurations for Fail2ban, so i Vim into this (as this is my favorite editor - use yours):
$ vim jail.conf
The first thing you should edit is the ignoreip-line under the [DEFAULT]-block. IP-addresses added to this (just with a space) will be ignored, and never blocked - so add your own machines ip, so you are sure that this will never block your own ip-address (12.34.56.78 in this example):
[DEFAULT]
...
ignoreip = 127.0.0.1 12.34.56.78
...
This is actually enough to get Fail2ban to work, with minimum configuration. There is also other things to lookout for, like the maxretry and the bantime (which i always make longer). If you scroll down you can also see options of configuring eg. httpd, ftp and postfix. Experiment a bit :-)
Fail2ban works as a service, and can be controlled through:
$ sudo service fail2ban [start|restart|stop|etc...]
So when all your configurations has been done, run the restart action to make them active:
$ sudo service fail2ban restart
Now you should be good! Test by logging into your machine with wrong password from another machine, and see what happens in Fail2ban's logs or by checking the iptables list:
$ iptables -L
Others
Check your fail2ban-log like this:
$ tail /var/log/fail2ban.log
The log will hold data about when it has been blocking ip-addresses and more.
On a half day Fail2ban already had blocked 11 ip-addresses on my machine:
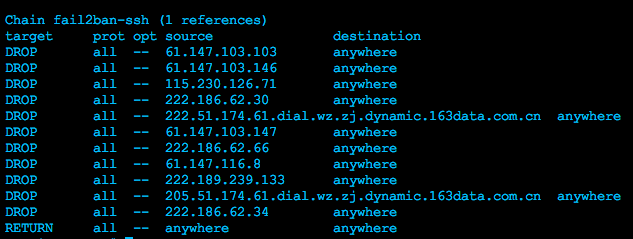
Bit of extra information on these:
With the same ip as the last block from Fail2ban, this would be the same if you did it yourself with iptables:
iptables -A INPUT -s 222.186.62.34 -j DROP
This line means that iptables append (-A) to the INPUT-table (INPUT) for IP-address 222.186.62.34 (-s/--source) and block/DROP the connection (-j). The port (--dport) 'anywhere' and protocol (-p) 'anywhere' has been said itself, because we have not defined them.
What does the different chains in iptables mean, where you can filter in the ip-addresses:
INPUT - connections incoming to this server
FORWARD - connections going through this server
OUTPUT - outgoing connections from this server
Read more about iptables here:
https://help.ubuntu.com/community/IptablesHowTo
Read more about Fail2ban here:
http://www.fail2ban.org/wiki/index.php/Main_Page